Ahoy, captains! The crypto seas may promise vast riches, but they are also teeming with cunning pirates waiting to plunder the unprepared. Hackers and scammers are relentless, crafting elaborate traps to exploit even the slightest lapse in judgment. Staying safe isn’t just an option—it’s your responsibility.
In The Whale Room, we believe every misstep is a lesson, and every cautionary tale a chance to grow wiser. As we dive into the stories of several members on the ship who fell victim to these perils, let this serve as a stern reminder: protecting your assets begins with knowing the dangers. The responsibility to stay informed and vigilant rests squarely on your shoulders. Let’s uncover exactly how these scams unfolded and what we must learn to outsmart those who seek to take what’s ours.
1. Dane: The Fake SMS Scam
Officer Dane was a seasoned trader and a careful member of The Whale Room. He thought he had seen it all—phishing emails, fake websites, and even compromised public Wi-Fi. But one morning, he encountered a new kind of scam: a fake SMS that almost slipped past his defences.
The message arrived early, just as Dane was sipping his coffee and preparing for a day of trading. The text read:
Dane froze. He wasn’t trading at the time, and the thought of unauthorized access to his account sent a wave of panic through him. Without thinking, he clicked the link in the message, which brought him to what appeared to be KuCoin’s support page.
The site looked legitimate, complete with KuCoin branding, a support chat box, and instructions to "verify your account to cancel the withdrawal."
It asked Dane to log in using his KuCoin username and password. Thinking he was protecting his funds, he entered his credentials and hit submit.
What Dane didn’t realize was that the SMS wasn’t from KuCoin at all. The link wasn’t associated with KuCoin.com while the message had a .click extension. It was a cleverly disguised phishing site designed to steal his login credentials.
The scammers, monitoring the fake site in real time, immediately used Dane’s credentials to access his real KuCoin account. They bypassed his SMS-based two-factor authentication by triggering a SIM swap attack, which gave them control of his phone number. Within minutes, they initiated multiple withdrawals, transferring his funds to anonymous wallets.
Dane first suspected something was wrong when he received an actual withdrawal confirmation email from KuCoin. By the time he logged into his account to investigate, his funds were gone.
Always click from the official page on X.com.
If you go to X.com, find the official website link on Kucoin’s page. Look at the number of followers. Sites like that have an insane number of followers.
2. LEARN TO UNDERSTAND HOW URL’s WORK.
I came across a website that explains clearly how to sport fake URL’s. Visit it here:
https://www.aura.com/learn/how-to-identify-fake-websites
Educate yourself. It is very easy to misunderstand a URL, but once you understand it, it becomes really easy to spot a fake URL.
3. Tom: Phishing Hooked Him
Captain Tom kept $50,000 in his exchange account. One morning, he received an email with the subject line: "Action Required: Update Your Account to Avoid Lockout." The email appeared legitimate, complete with official branding and a link to "secure" his account.
Thinking it was urgent, clicked the link and followed the instructions.
The webpage looked identical to his exchange’s login page.
Username? Password? Done. He even double-checked that his credentials were updated correctly. Feeling accomplished, he logged off and took his trusty pup for a walk.
What he didn’t know was that the link directed him to a fake phishing site controlled by hackers. They immediately used his credentials to access his real account, withdraw his funds, and disappear into the depths of the crypto sea.
But while strolling along the coast, Tom’s phone buzzed. A notification. His $50,000? Gone
4. Here is a similar scam
5. More About Emails
6. Sarah: The Public Wi-Fi Trap
Sarah was eager to check her portfolio while sipping coffee at her favourite café.
The café’s free public Wi-Fi offered an easy way to connect, and without much thought, Sarah clicked "connect" and launched her browser. Shortly after, she opened an email with the subject line: "Unusual Account Activity Detected – Verify Immediately." The message appeared urgent and professional, with her exchange’s logo at the top and a link to log in and review her account.
Her pulse quickened. Could someone have attempted to access her funds? The email read: "To protect your account, please confirm your credentials immediately." She felt a mix of anxiety and responsibility, thinking, "Better safe than sorry." She clicked the link and was taken to a page that looked exactly like her exchange’s login portal.
She typed her username. Password? Done. Once she logged in, she was relieved to see her balance untouched, and there were no signs of suspicious activity. Reassured, she closed the browser and took another sip of her coffee.
What Sarah didn’t know was that the email she had received wasn’t from her exchange at all—it was from a hacker. The link had directed her to a phishing site, an identical replica of her exchange’s login page. Every keystroke she entered was sent directly to the hacker in real time.
Worse still, the café’s public Wi-Fi was compromised. The hacker, connected to the same network, used a “man-in-the-middle” attack to monitor data being transmitted. They intercepted her credentials as she typed them.
Just as she started packing up to leave, her phone buzzed. A notification: "$10,000 withdrawal completed." Confused, she reopened her exchange app only to see a second transaction processing. By the time she managed to freeze her account, her funds had been siphoned off into untraceable wallets.
Sarah learned a hard lesson that day. Public Wi-Fi, no matter how convenient, is dangerous terrain for crypto traders.
7. Liam: The AI-Generated Video Trap
Trader Liam was scrolling through YouTube late one evening, searching for market insights and updates on Bitcoin. As a regular in The Whale Room, Liam knew the importance of staying informed, and he often followed Michael Saylor’s interviews for insights into Bitcoin’s long-term prospects.
That night, a live stream on YouTube caught his eye. The title read: “MICROSTRATEGY EVENT: Michael Saylor Announces Bitcoin Bonus Giveaway!” Intrigued, Liam clicked the video.
The live stream featured Michael Saylor, confidently speaking about Bitcoin’s future. In the video, he announced a limited-time offer:
“To celebrate Bitcoin reaching new milestones, MicroStrategy is doubling Bitcoin investments! Send any amount of BTC to our official address, and we’ll send back double the amount as a thank-you to the crypto community.”
On the screen, a QR code and Bitcoin wallet address appeared, alongside text urging viewers to act quickly as the offer was only valid during the live stream. The production looked polished, with MicroStrategy’s logo and visuals that mirrored their official branding.
Liam, feeling both excited and skeptical, checked the comments section. It was filled with people thanking Michael Saylor for the opportunity, claiming they’d already received their doubled Bitcoin. The chat was fast-paced, with messages like:
“Just sent 0.5 BTC, got 1 BTC back! Thank you, Michael!”
“Legit! This is the best giveaway ever!”
Seeing the overwhelming “proof” in the comments and with the clock ticking, Liam decided to take a chance. He scanned the QR code and sent 0.1 BTC to the address. Feeling confident, he waited for the doubled return to arrive.
Minutes turned into hours, and no Bitcoin came back. Suspicious, Liam tried to revisit the video, but it had been taken down. Realization dawned on him: he had been scammed. The video wasn’t an official MicroStrategy production—it was an AI-generated deepfake designed to mimic Michael Saylor.
8. Jake: Malware Mayhem
Navigator Jake was on a roll. His trades were precise, his portfolio grew, and he had a knack for timing market shifts. Jake prided himself on being tech-savvy, often scouring the web for market insights and crypto strategies to stay ahead of the curve.
One day, an email landed in his inbox with the subject line: "Exclusive Report: Bitcoin’s Next Big Move Revealed!" The sender appeared to be from a well-known crypto analytics platform that Jake frequently follows. Excited at the prospect of gaining insider knowledge, he eagerly opened the email. Inside, a neatly written message invited him to download the attached PDF report.
Jake clicked the attachment, a file labelled "CryptoTrends2024.pdf,” and opened it without hesitation. Nothing seemed to happen—the file didn’t load, and Jake assumed it was a broken link. Shrugging it off, he deleted the email and went back to his day.
What Jake didn’t realize was that the attachment wasn’t a report at all—it was a cleverly disguised piece of malware. As soon as he opened the file, the malware began working silently in the background, scanning his computer for sensitive data. It didn’t take long for the program to locate a file on Jake’s desktop labelled "My Wallet Keys.docx."
The file contained a list of private keys for various wallets Jake managed. The malware transmitted this information to the hacker controlling it, who immediately began accessing Jake’s wallets. Within minutes, Jake’s funds were being siphoned off to untraceable addresses.
A few hours later, Jake opened his wallet to check on a recent deposit, only to find his balance at zero.
Jake’s downfall came from a combination of trust and complacency. He assumed the email was legitimate because it came from a name he recognized and overlooked basic cybersecurity practices, like scanning attachments or verifying the sender’s authenticity.
Jake learned the hard way that not every opportunity is what it seems, and that malware can wreak havoc on even the most experienced traders.
9. Other Warnings Related To Wallets
Do not trust any free tokens that are distributed to your wallet.
https://www.pocketuniverse.app/ is an extension that you can add to your browser. When you click through your wallet to a link it will warn you when a website is a possible scam. They even offer insurance in case you got scammed.
10. Mia: The Telegram Lurker Trap
Mia, a diligent trader in The Whale Room, ran into trouble when she couldn’t log into her KuCoin account. Feeling frustrated and eager to fix the issue quickly, she turned to the official KuCoin Telegram group for help. With thousands of members and an active chat, the group seemed like the best place to find answers.
She posted her question:
"Hi, I can’t log into my KuCoin account. Can anyone help?"
Before long, someone responded—but not in the group itself. Mia received a direct message from someone with a KuCoin logo as their profile picture and the username "KuCoin_AdminSupport." The message read:
"Hello Mia, I saw your message in the KuCoin group. I’m an admin here to assist you. Let’s get this resolved quickly to protect your funds. Can you confirm your email and recent login attempts?"
Relieved that someone was willing to help, Mia shared her email and briefly described her issue. The “admin” replied almost immediately:
"Thank you for the information. It looks like we need to verify your account to restore access. Please provide your 2FA code so we can complete the recovery process."
The urgency in the tone and the promise of quick resolution made Mia hesitate, but the “admin” pressed on:
"Mia, if we don’t resolve this now, your account could remain at risk. Please send the 2FA code immediately so we can secure your funds."
Feeling the pressure, Mia complied and shared the code. Within minutes, she received notifications of unauthorized withdrawals. Her KuCoin account was being emptied, and every attempt she made to stop it failed. By the time she reached out to KuCoin’s real support team, her funds were gone—transferred to anonymous wallets.
I personally tested this. I went on the KuCoin chat on Telegram and pretended I couldn’t login into my KuCoin account. A minute later I had 4 so-called admins offering support.
Do not reply to ANY Telegram private support. The moment someone comment and tell you to DM him because he can help, RUN!
In one of my recent posts, a reader asked advice about how to register on an exchange. And soon he received a reply. “I’m here to help you Todd, I just sent you a message”
Even if it is from a person with the best intentions, you will never know if it is a scammer.
DO NOT respond to messages like these. If you need help, ask on a trusted platform such as our Whale Room and expect a reply on that same server. The moment you receive a private message offering help…well you know now what to do, right?
Block your DM’s on Discord!
11. Leo: Password Reuse Disaster
Leo was a rising star in The Whale Room but had a dangerous habit—reusing passwords across multiple exchanges. He thought, It’s simple, and no one will figure it out. One day, one of those exchanges experienced a data breach, exposing Leo’s email and password.
The exchange assured users that the passwords were encrypted, but Leo didn’t pay much attention—after all, he didn’t keep much on that exchange.
The hackers, however, didn’t stop there. Using the stolen information, they ran Leo’s email and password combination through other major exchanges. To their delight, they discovered that Leo used the exact same credentials on several platforms.
Within minutes, the hackers had logged into his accounts, bypassing any weak security measures like SMS-based 2FA. They initiated withdrawals, sending Leo’s funds to anonymous wallets.
Leo first noticed something was wrong when he received a withdrawal confirmation email from his primary exchange. He quickly logged in and saw the damage—thousands of dollars drained in a matter of minutes. Desperately, he tried to lock his accounts, but the hackers had already cleared out everything.
Leo’s mistake was a common one: reusing passwords across multiple platforms. He thought simplicity was the key to convenience, but it turned out to be the key to his undoing. This oversight allowed hackers to exploit a single breach and wreak havoc across all his accounts.
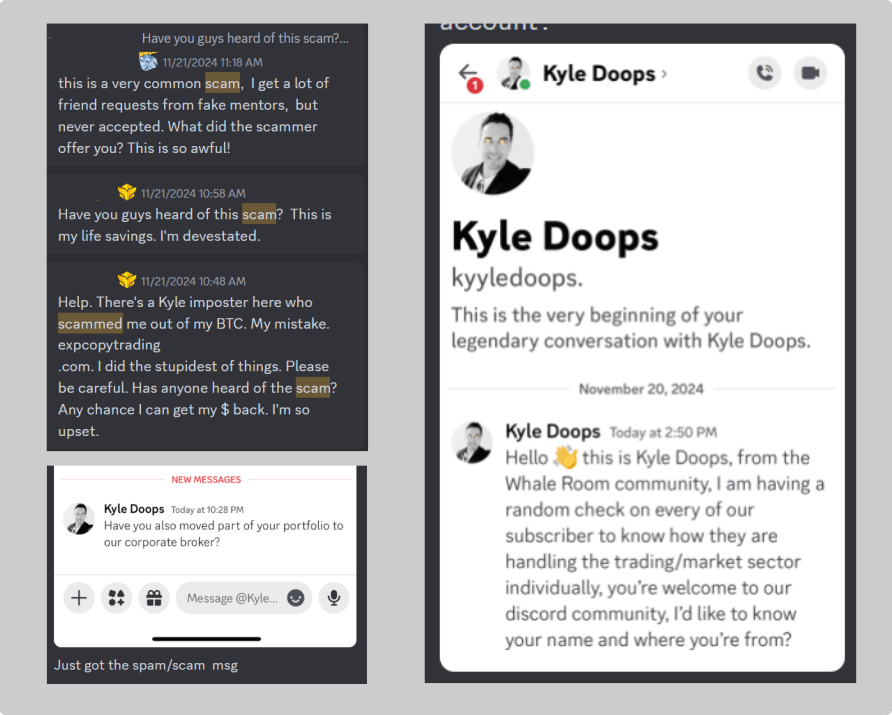
12. Eric: The Fake Captain DM
Eric, an active member of The Whale Room, admired Kyle, the Captain of the Ship. Known for his unparalleled ability to map Bitcoin’s next move and identify breakout trades, Kyle was a trusted figure in the community. So, when Eric received a direct message from someone with Kyle’s profile picture, he felt both honoured and excited.
The message read:
"Hey Eric, I’ve been watching your progress in the group. You’ve got real potential. If you’re interested, I can personally help grow your portfolio. I’ll handle the trades for you and show you how it’s done at a higher level."
The sender explained that all Eric needed to do was transfer funds to a provided wallet address, and the “Captain” would execute trades on his behalf. The tone was casual yet authoritative, perfectly mimicking Kyle’s leadership style. To make it sound like a once-in-a-lifetime opportunity, the message added:
"I don’t usually offer this to members, but I see potential in you. Let’s aim for significant growth over the next few weeks. I’ll only take a small fee from the profits."
Eric, flattered and eager to take advantage of Kyle’s expertise, felt this was an incredible opportunity. After all, Kyle’s reputation for calling winning trades was unmatched. The offer felt genuine—who better to trust than the Captain of the Ship?
Eric transferred 0.5 BTC to the wallet address provided, expecting updates on the trades soon. Hours turned into days, but the “Captain” didn’t message back. Growing concerned, Eric posted in the public Whale Room chat, asking about Kyle’s offer.
The real Kyle was quick to respond:
“Eric, that wasn’t me. I would never DM anyone asking for funds or offering to trade on their behalf. You’ve been scammed.”
Eric’s heart sank. He realized the wallet he’d sent his funds to was controlled by scammers. They’d used Kyle’s profile picture and conversational tone to manipulate him into trusting them.
This is exactly why Whale Room members survive the harshest waters of the crypto seas. It’s so easy to fall for just one trap, but within a strong community, you always have the power to ask, verify, and double-check before making any move.
Never think it can’t happen to you—scammers thrive on overconfidence. Together, we navigate safely, sharing knowledge and staying one step ahead of those who lurk in the shadows. Join us and let’s sail securely toward success. 🌊 Sign Up Here
13. Some Other Fake Kyle Incidents
14. Maya: The SIM Swap Heist
Maya was a diligent trader, always keeping her portfolio updated and her trades strategic. She had a solid grasp of the markets but overlooked one critical vulnerability: her phone number.
One afternoon, Maya’s phone suddenly lost service—no calls, no texts, no data. She assumed it was a minor issue and decided to troubleshoot later. What she didn’t know was that hackers had executed a SIM swap, convincing her mobile provider to issue them a new SIM card tied to her number.
With control of her phone number, the hackers reset her exchange account passwords, bypassing SMS-based 2FA. Within minutes, they gained access to her accounts, drained her wallets, and sent her funds to anonymous addresses.
Maya realized something was wrong when she tried to log into her exchange and found her credentials didn’t work. By the time she contacted her provider and regained control of her number, it was too late. Her funds were gone.
Maya learned the hard way that relying on SMS-based 2FA alone is a major risk in the crypto world. Hackers can exploit weaknesses in mobile provider security to gain access to your accounts, making other forms of 2FA essential.
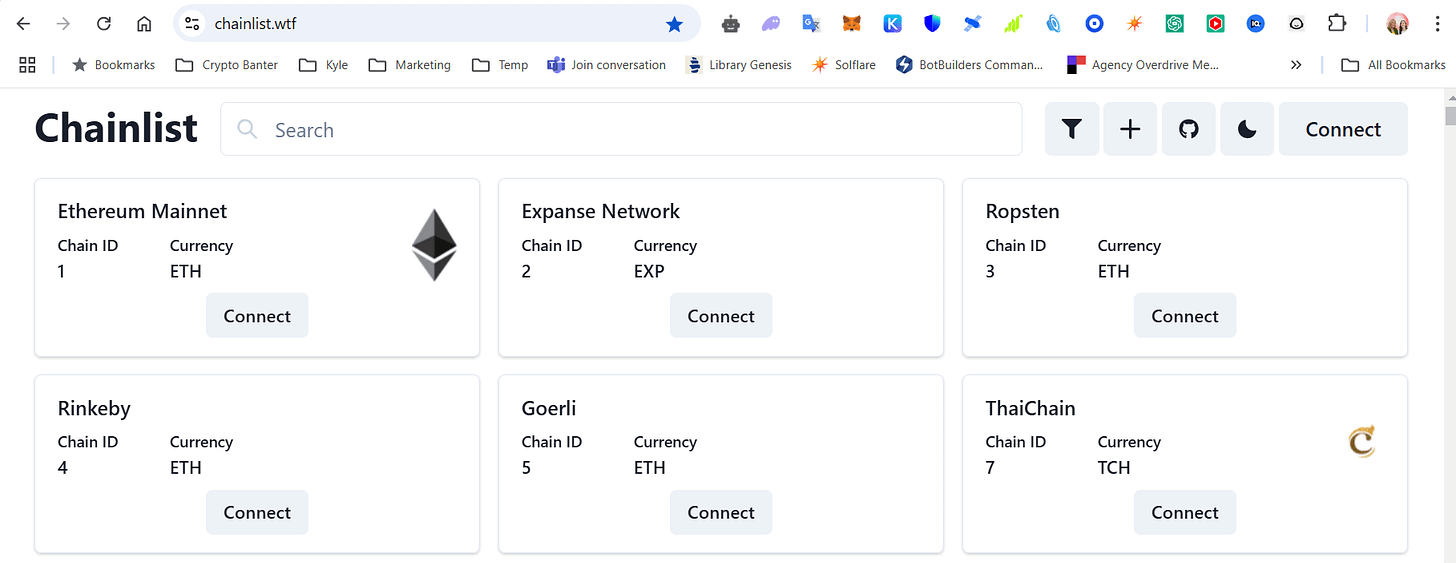
15. Jules: The Chainlist Imposter
Jules, an experienced trader and longtime Whale Room member, often explored new opportunities in the DeFi world. One day, while setting up a new project, he needed to add a blockchain network to his MetaMask wallet. Knowing that Chainlist.org was the go-to platform for such tasks, he quickly Googled "Chainlist" to find the link.
The top result wasn’t Chainlist.org but a similar-looking site with a different extension
At first glance, it didn’t look exactly like the original, but it seemed professional enough. Jules thought, “This must be the right one—it’s at the top of Google’s search results.”
Upon visiting the site, Jules noticed a prompt to “Connect Wallet” and add the network automatically. It seemed convenient, so he clicked the button and approved the connection request in MetaMask. But what Jules didn’t realize was that this was a scam site. Instead of adding a legitimate network, it added a malicious smart contract with hidden permissions to transfer funds.
Minutes after approving the connection, Jules received a notification from MetaMask: funds had been sent from his wallet to an unknown address. He frantically checked his transaction history but could do nothing—the scammers had drained his wallet.
Later, Jules learned from The Whale Room that the real Chainlist.org provides its official link through trusted channels, like their verified X.com (formerly Twitter) account. Had he double-checked the link there, he could have avoided the fake site.
16. Dana: The Discord Giveaway Trap
Dana, a passionate crypto enthusiast, joined a new Discord server to participate in a project she had been excited about. The server seemed active and legitimate, and Dana eagerly explored the various channels. Among them was a “Verify Humanity” channel, a common feature in crypto Discords, where users usually complete simple steps to access the rest of the server.
What Dana didn’t know was that the server admins weren’t vigilant about managing permissions. A scammer had managed to post a link in the channel, cleverly disguised as part of an official giveaway event. The message read:
“Congratulations! To celebrate our project launch, today we’re giving away free rewards to verified users. Claim your bonus here: [maliciouslink.xyz].”
The link led to a professional-looking site branded to resemble the project’s official pages. The site instructed users to connect their MetaMask wallets to claim their rewards. The promise of free tokens seemed too good to pass up, and Dana, excited at the thought of being part of the project’s early supporters, hurried to connect her wallet.
As soon as she approved the connection, the scam site executed a malicious contract. Funds began disappearing from Dana’s wallet almost instantly. Notifications of unauthorized transactions flooded her phone. Confused and panicking, she disconnected her wallet, but by then, the damage was done—her funds had been drained.
Dana later discovered the truth: the link had been posted by a scammer lurking in the server. The admins had allowed open posting permissions, enabling bad actors to exploit the channel and deceive users.
17. About Free Airdrops
18. Chris: Clicked Into a Trap
Chris prided himself on being cautious, but he let his guard down one fateful day. An email claiming to be from a leading crypto analytics platform offered an "Exclusive Report on Bitcoin's Next Big Move."
The sender appeared to be a respected crypto analytics platform Chris often followed, so he didn’t hesitate to open it. Inside was a simple invitation to download an attached PDF report titled “CryptoTrends2024.pdf.”
Without much thought, Chris clicked the file. Nothing happened. Assuming it was a broken link, he shrugged it off and deleted the email.
What Chris didn’t know was that the attachment wasn’t a report—it was malware. As soon as he opened the file, the malware activated, silently scanning his computer for sensitive data. It found what it was looking for in a file Chris had named “My Wallet Keys.docx.”
The malware transmitted his private keys to the hacker, who immediately began draining Chris’s wallets. A few hours later, when Chris logged in to check a recent transaction. His wallet balance was zero.
He tried to trace the outgoing transactions but realized the funds had already been sent to untraceable addresses.
Chris’s downfall came from a single moment of misplaced trust. By clicking on an attachment without verifying its source, he unknowingly opened the door to disaster.
19. Finn: The Telegram Trading Call Trap
Finn, a budding trader and loyal member of The Whale Room joined a Telegram group that promised the best trading signals in crypto. The group was vibrant and active, with admins posting frequent updates, “winning trades,” with 20x leverage, and bragging about huge returns.
Initially, Finn followed some of the free trading calls. While his results were underwhelming, the group’s updates always highlighted massive wins. Each screenshot they posted showed incredible profits, accompanied by comments like: “Premium members are making bank today!” Feeling like he was missing out, Finn decided to dive deeper.
The admins soon rolled out an exclusive opportunity:
“Why stress over trades? Let us handle everything for you. With our expertise, you’ll see 3–5x growth in just a month! Sign up on our platform and let us take care of the rest.”
They directed him to a website that, at first glance, appeared professional. It had a clean design, a dashboard to track trades, and promises of exponential growth. Trusting their claims, Finn deposited 0.3 BTC into the platform, excited to let the “experts” grow his funds.
After the deposit, Finn’s account still showed a 0 balance on the website.
When Finn tried to cancel his subscription and requested a refund, he encountered the first hurdle. His refund request was met with vague messages, and support responded with excuses about “market delays” and “technical issues.” Feeling uneasy, Finn decided to dig deeper.
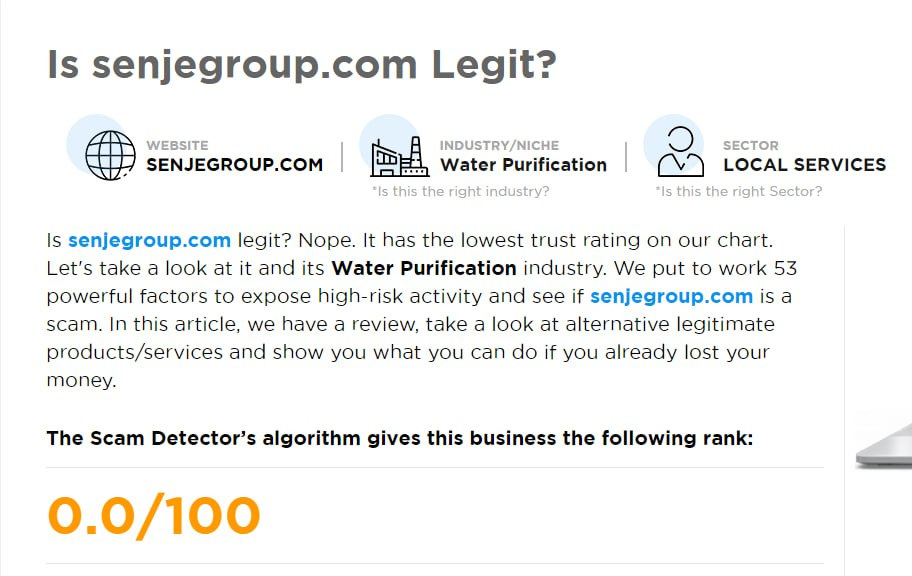
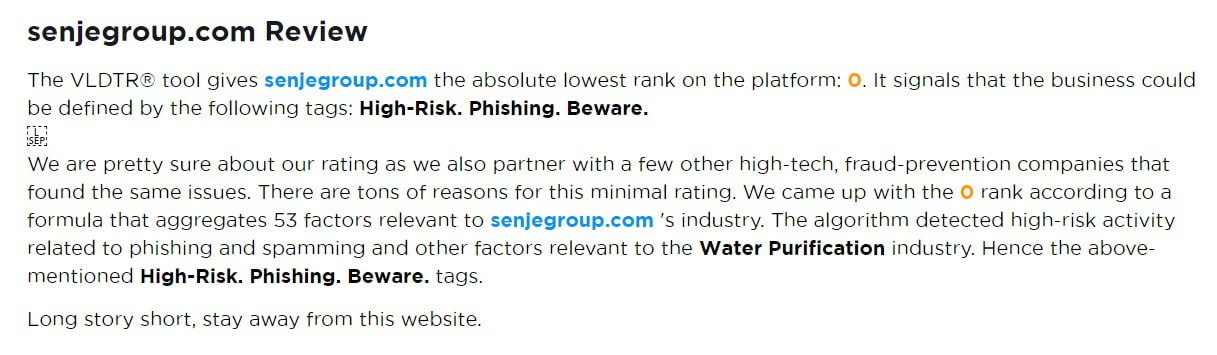
What Finn discovered shocked him. Upon closer inspection of the website, several glaring red flags became obvious. There was no link to any terms and conditions, a critical omission for any legitimate financial platform. The About Us page was riddled with stock photos of smiling “team members” that could be found with a reverse image search. The website also lacked genuine testimonials—just vague claims of success without any identifiable user stories.
Even more troubling was the fact that the admins marketed themselves as financial advisors, but their credentials were nowhere to be found. A quick online search revealed scam warnings from other traders who had fallen into the same trap. In fact the same URL was previously used to promote water purification services.
Finn had ignored several subtle but critical warning signs, dazzled by the allure of quick profits. The Telegram group, the flashy website, and the constant updates were all part of an elaborate ruse designed to lure traders into depositing funds that they’d never see again.
20. Alex: The Café Camera Capture
Alex, an eager trader and regular at The Whale Room, often worked from his favorite café. It was a bustling spot, perfect for reviewing market trends while enjoying a latte. On one such day, Alex logged into his exchange account to check on an open trade. He typed his username and password quickly, his focus entirely on the market charts displayed on his laptop.
What Alex didn’t notice was a small camera discreetly mounted behind him, angled perfectly to capture his laptop screen. A hacker in the café had set up the camera to record unsuspecting patrons as they entered sensitive information like passwords.
The hacker later reviewed the footage, zooming in on the moments when Alex typed his credentials. Armed with Alex’s login details, the hacker logged into his exchange account and initiated withdrawals. Since Alex hadn’t enabled two-factor authentication, there was nothing to stop the hacker from draining his funds.
Alex only realized what had happened when he received a withdrawal confirmation email. By the time he logged in to freeze his account, it was too late—the funds were gone, transferred to anonymous wallets.
Even the best defences can fail if you’re not mindful of your surroundings. Alex’s oversight reminds us that security is not just about technology but also about vigilance in the real world.
21. Ella: Public Wi-Fi Spyware
Ella, a meticulous trader and longtime member of The Whale Room, prided herself on her discipline and sharp instincts. One day, while attending a co-working space, she noticed a sudden market movement and decided to make a quick trade.
She connected to the co-working space’s free public Wi-Fi and logged into her exchange account. Everything seemed normal as she executed her trade and reviewed her portfolio. Confident she’d capitalized on the market shift, she logged out and returned to her tasks.
What Ella didn’t know was that the network had been compromised by a hacker using spyware. The hacker, lurking on the same network, monitored Ella’s activity in real-time. By intercepting her connection, the hacker captured her login credentials, including her username and password.
Within minutes, the hacker logged into Ella’s account, bypassed her weak SMS-based two-factor authentication, and initiated withdrawals. By the time Ella noticed the notifications, her funds were already gone, transferred to untraceable addresses.
Ella’s mistake wasn’t logging into her exchange—it was trusting a public Wi-Fi network without taking precautions like using a VPN to encrypt her activity.
The most effective way to protect yourself from these types of attacks is by using a virtual private network (VPN). A VPN encrypts your data during transmission, making it impossible for hackers to intercept your sensitive information or gain access to your cryptocurrency. We have done our research and looked for the most reliable VPN. You can get it here.
22. Riley: The No-2FA Blunder
Riley, a dependable member of The Whale Room, was known for his straightforward trading approach. He always followed market updates and kept his portfolio diversified, but his focus on trading meant he overlooked one critical detail: setting up two-factor authentication (2FA) on his accounts.
One day, Riley received an email with the subject line: “Urgent: Suspicious Login Detected.” The message appeared to be from his exchange, warning that someone had attempted to access his account. The email urged him to “verify his credentials immediately” to secure his funds.
Without hesitation, Riley clicked the link, which led him to a page identical to his exchange’s login portal. Feeling a sense of urgency, he entered his username and password.
The email, however, wasn’t from his exchange. It was from hackers running a phishing scam. The link had directed Riley to a fake website that captured his credentials in real time. The hackers quickly logged into his real account, bypassing security since Riley hadn’t set up 2FA.
Within minutes, the hackers initiated large withdrawals. Riley noticed something was wrong when he received a confirmation email for a transaction he hadn’t made. He rushed to log into his account but found his balance drained, with no way to recover the stolen funds.
Riley learned a painful lesson: while strong passwords are a good start, they aren’t enough. Without 2FA, even a single phishing email can spell disaster.
🐋 Swim with the Whales
Welcome to the Whale Room, where precision trading meets extraordinary gains. Once again, our expert traders have been riding the waves of success, delivering incredible results.
Christo Columbus: This trade exceeded all expectations, securing a 114% gain on $XRP. It's yet another testament to his unparalleled insight and execution.
Farouk the Sea Scalper: First limit order hit on $RUNE, up 28%. Manage this trade and take profit whenever you want—thumbs up if you’d like more limit orders! And about the $WIF trade—I’m still in it! I thought I was stopped out, but it literally missed my stop-loss. Lucky me! Let me know if you guys are still in it too—currently up 214%.
Let us continue to celebrate the remarkable achievements of our traders and community. Here's to navigating the crypto seas with precision and confidence. Look at what our members achieved recently.
Kyle, the Captain of the Ship, is not just a master of charts and trading strategies—he’s the anchor of trust in the Whale Room. Known for his precision, transparency, and dedication, Kyle's calls have consistently delivered extraordinary results. Beyond his unmatched skill, it’s his integrity and genuine commitment to helping others succeed that sets him apart, making him a true leader in the crypto seas.
Conclusion: Security is Survival
These stories from our crew illustrate one undeniable truth: even the smallest vulnerabilities can lead to catastrophic losses. Whether it’s clicking on the wrong link, neglecting to set up 2FA, or reusing passwords, hackers thrive on human error.
In The Whale Room, we believe that knowledge is the best defence. Each mistake is a lesson, each loss a warning. Let these tales remind you to stay vigilant, proactive, and always one step ahead.
Remember, captains: The price of freedom in the crypto seas is eternal vigilance. Stay sharp, stay secure, and let’s sail toward a future filled with fortune and success. 🌊
Not your keys, not your crypto.
Ready to take control of your crypto journey and protect your hard-earned assets? In The Whale Room, our members are always up to date with the latest scams, threats, and strategies to stay secure in the ever-changing crypto seas.
Beyond trading success, we’re committed to ensuring you have the knowledge and tools to protect your portfolio. Don’t sail these waters alone—join a community that’s as focused on security as it is on success. 🌊 Sign Up Here
Tell me in the comments below—have you ever been scammed? How did that happen? I read all the comments.
Don’t wait. Take advantage of our Black Friday special!—click here to join the Whale Room now and start swimming with the pros!
Help Spread the Word!
If you’d like to help me spread the word, all you have to do is send one friend a personal email where you tell them all about today’s blog.
Follow Kyle on X: Kyle Doops
Watch Kyle’s YouTube channel: Kyle's YouTube
Follow us on our new Whale Room page X page here.
Chat soon!
Inet Kemp